Search the FirstSpirit Knowledge Base
- Crownpeak Community
- :
- FirstSpirit
- :
- Knowledge Base
- :
- Helpful Information
- :
- Addendum for Manual for Administrators: Kerberos w...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Helpful Information
Addendum for Manual for Administrators: Kerberos with AES as encryption type
How to create a Kerberos keytab file
with support for AES128 or AES256
How to enable AES256 support in the JVM
This addendum replaces
PDF: FirstSpirit Manual for Administrators
Chapter: 4.3.4.5 Kerberos ticket (integrated Windows login)
Paragraph: Creating the Kerberos-Keytab file in the example under Microsoft Active Directory
Notes
- Firstspirit Server requires Java 1.8.0_51 or newer for Kerberos if Java 8 is used: Java-Bug 8078439, blog post
- In some Active Directory environments, Internet Explorer 11 on Windows 7 and Windows 8 is sending Tickets of new standard NEGOEX depending on the Active Directory configuration which is currently not supported by Java 7 and 8 (Bug 8068516 and 6773898). Workaround: use Chrome, Firefox or Internet Explorer in compatibility mode in these environment.
Problem:
If Kerberos SPNEGO based authentication is enabled and configured in FirstSpirit and the following error message is written to firstspirit5/log/fs-server.log or tomcat/log/firstspirit.log, the AES256 support within the JVM used for the FirstSpirit or Tomcat is not enabled:
ERROR 01.02.2013 12:34:00.000 (de.espirit.firstspirit.server.authentication.KerberosLoginModule):
login failed! Failure unspecified at GSS-API level
(Mechanism level: Encryption type AES256 CTS mode with HMAC SHA1-96 is not supported/enabled)
If the following error message is written to firstspirit5/log/fs-server.log or tomcat/log/firstspirit.log, the SPN entries for the encryptions types AES128 or AES256 are missing in the keytab file given in firstspirit5/conf/fs-jaas.conf:
ERROR 01.02.2013 12:34:00.000 (de.espirit.firstspirit.server.authentication.KerberosLoginModule):
login failed! Defective token detected
(Mechanism level: GSSHeader did not find the right tag)
Solution:
To create the file on a Kerberos server in a Microsoft Active Directory Domain, Windows Support Tools must be installed; they are supplied by Microsoft on the installation media of the operating system or can be downloaded from http://microsoft.com.
First, a normal user account has to be created on the Windows Domain Controller. This account must not be used for any other services than this keytab file as the password will be changed in this process and further changes of the password would invalidate the keytab file. The account does not need to assigned to any groups. To mark the user name as technical account for the Kerberos based service, a good name pattern is HOSTNAME-PROTOCOL, in this example elstar-HTTP is used. Use "http" also for "https". For the password, just enter any random text as it is overwritten in the next step. The parameters for the user account must be set as follows:
- password never expires: enabled
- user cannot change password: enabled
- do not trust user for delegation: enabled (not required for FirstSpirit, but increases security)
- use DES encryption for this account: DISABLED
- support for AES128: enabled (if you want to allow encryption with 128 bit key length)
- support for AES256: enabled (if you need encryption with 256 bit key length)
Screenshot while chaning user parameters:
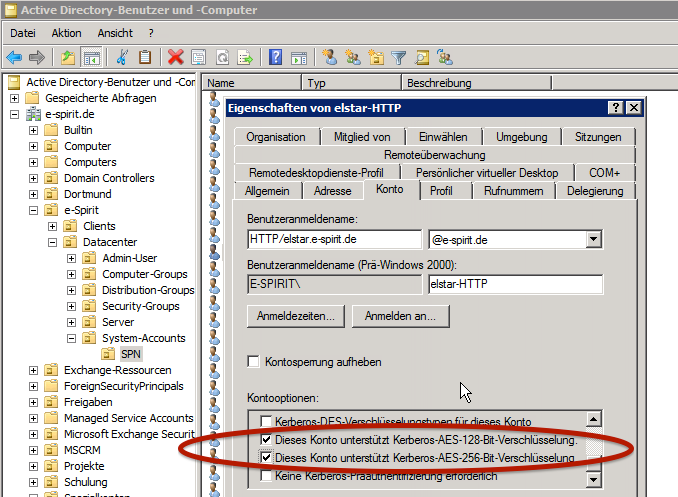
Next, the SPN record is created, bound to the previously created user account and exported as keytab file. In addition to the previous documentation of FirstSpirit, we don't create a keytab file with just one encryption method, but instead create a combined file which containts SPN private keys for any encryption method supported within this Kerberos Realm. All these actions are automatically performed on the Windows Domain Controller by the command-line tool ktpass.exe from the Windows Support Tools:
ktpass -princ HTTP/elstar.mydomain.net@MYDOMAIN.NET
+rndpass -mapuser elstar-HTTP \-crypto ALL –ptype KRB5_NT_PRINCIPAL -out elstar-http.keytab
Note, that elstar-HTTP is the sample user account name written as one single word, not two parameters like "elstar -http".
Documentation for ktpass.exe: http://technet.microsoft.com/de-de/library/cc779157(v=ws.10).aspx
If the version of the ktpass used does not provide +rndpass, a manually entered random password can also be used here via -pass PASSWORT.
A limitation to just one encryption type is not possible via changing the parameter -crypto from ALL to RC4-HMAC-NT or AES256-SHA1 as at least Windows 2008R2 then would offer a wrong encoded ticket to the client.
You can only map one SPN record to any user account, so you need to create multiple user accounts for hosts with many virtual web server names.
For error analysis, the list of all Service-Principal names of the user account can be displayed as follows and it should show one entry only:
setspn -l elstar-HTTP
To remove a SPN from a user account:
setspn -d HTTP/elstar.mydomain elstar-HTTP
The keytab file created with ktpass.exe must now be copied onto the FirstSpirit server or the external application server, to the path given in fs-jaas.conf at parameter keyTab, for instance /opt/firstspirit5/conf/elstar-HTTP.keytab.
The entries within the keytab file can be listed and checked with the following command calls:
Unix:
klist -ke elstar-HTTP.keytab
kinit -V -k -t elstar-HTTP.keytab HTTP/elstar.domain.net@DOMAIN.NET
Windows:
c:\program files\java\jdk1.7.0_51\bin\ktab -l -e -k elstar-HTTP.keytab
Mac OS X:
ktutil -k elstar-HTTP.keytab list
As result, the list of all encryptions types, all with same KVNO (key version number), should be shown.
Now continue with the configuration of the file firstspirit5/conf/fs-jaas.conf as shown in chapter 4.3.4.5 Kerberos ticket (integrated Windows login).
How to enable AES256 support in the JVM
Oracle Java is by default limited to 128 bit key lengths for AES and other encryption algorithms. To enable larger key lengths like 256 bit, the "Java Cryptography Extension (JCE) Unlimited Strength Jurisdiction Policy Files" are required for Java 7 from http://www.oracle.com/technetwork/java/javase/downloads/jce-7-download-432124.html and Java 8 from http://www.oracle.com/technetwork/java/javase/downloads/jce8-download-2133166.html and need to be installed on the Java installation used for the FirstSpirit Server and if an external Web Application Server is used also for that. The installation instruction is given in the file READM.txt of the download package.
The installation is only required on the server, not the clients as the Kerberos authentication is done by the Web Browser on the client, not the JRE.
To check, which Kerberos ticket encryption types are supported by your JVM, use the following Java program:
KerberosEncryptionTypes.java:
/*
Lists all Kerberos Ticket encryption types this JVM supports.
If requested type is missing, install
"Java Cryptography Extension (JCE) Unlimited Strength Jurisdiction Policy Files"
http://oracle.com/technetwork/java/javase/downloads/jce-7-download-432124.html
compile: javac KerberosEncryptionTypes.java
start: java KerberosEncryptionTypes
source: https://community.oracle.com/thread/1527582?tstart=-4
*/
import sun.security.krb5.internal.crypto.EType;
import sun.security.krb5.EncryptionKey;
class KerberosEncryptionTypes {
public static void main(String[] args) throws Exception {
for (int i: EType.getBuiltInDefaults()) {
String t = EType.getInstance(i).toString();
String e = "?";
switch (i) {
case 1: case 3: e = "DES"; break;
case 16: e = "DESede"; break;
case 17: e = "AES128"; break;
case 18: e = "AES256"; break;
case 23: e = "ArcFourHmac"; break;
}
System.out.print("EType: (" + i + ") " + e + " " + t.toString());
System.out.println(new EncryptionKey("test".toCharArray(), "test", e));
}
}
}
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Falls die Anmeldung über Kerberos nicht funktioniert und die Überprüfung der Konfiguration des Browser keine Fehler zeigte, kann zumindest für Mac OS X oder Linux als Client testweise ein Anmeldeticket mit vorgegebenem Kryptoverfahren erzeugt werden, um zu testen, ob es nur mit einem der Verfahren funktioniert:
Beispiele:
kgetcred -e aes256-cts-hmac-sha1-96 HTTP/elstar.e-spirit.de@E-SPIRIT.DE
kgetcred -e arcfour-hmac-md5 HTTP/elstar.e-spirit.de@E-SPIRIT.DE
Für Windows noch noch nach einer Testmöglichkeit gesucht...
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Red Hat does not ship or support the Java Cryptography Extension Unlimited Strength Jurisdiction Policy File. You need to download the extension files from Oracle.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Additional debugging information can be enabled with adding the following JVM parameter in fs-wrapper.conf if using Jetty and setenv.sh if using Tomcat:
-Dsun.security.krb5.debug=true
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Additional debugging information can be enabled with adding the following JVM parameter in setenv.sh if using Tomcat:
-Dsun.security.krb5.debug=true
Or the following additional line if using Jetty:
wrapper.java.additional.300=-Dsun.security.krb5.debug=true
Sample log of a successful Kerberos authentication with log level DEBUG set in fs-logging.conf. The output is written to fs-wrapper.log when using Jetty or catalina.out when using Tomcat. Only with lines "KeyTab: load" and "KeyTabInputStream" the successfull read of the keytab file can be verified. All other lines regarding keytab only mirror the configuration setting as text without any verification.
INFO | jvm 1 | 2014/12/15 16:38:36 | DEBUG 15.12.2014 16:38:36.845 (de.espirit.firstspirit.server.authentication.AuthenticationManagerImpl): [1047786894] login context 'websso' created.
INFO | jvm 1 | 2014/12/15 16:38:36 | DEBUG 15.12.2014 16:38:36.850 (de.espirit.firstspirit.server.authentication.AuthLoginContext): [1047786894] login configuration 'websso' created.
INFO | jvm 1 | 2014/12/15 16:38:36 | DEBUG 15.12.2014 16:38:36.850 (de.espirit.firstspirit.server.authentication.AuthLoginContext): [1047786894] login...
INFO | jvm 1 | 2014/12/15 16:38:36 | DEBUG 15.12.2014 16:38:36.853 (de.espirit.firstspirit.server.authentication.AuthenticationManagerImpl): [1047786894] initialize...
INFO | jvm 1 | 2014/12/15 16:38:36 | DEBUG 15.12.2014 16:38:36.856 (de.espirit.firstspirit.server.authentication.AuthenticationManagerImpl): [1047786894] login: [FSTicketLoginModule/LoginModuleControlFlag: sufficient]
INFO | jvm 1 | 2014/12/15 16:38:36 | DEBUG 15.12.2014 16:38:36.856 (de.espirit.firstspirit.server.authentication.AuthenticationManagerImpl): request for callbacks handled without c/s roundtrip.
INFO | jvm 1 | 2014/12/15 16:38:36 | DEBUG 15.12.2014 16:38:36.856 (de.espirit.firstspirit.server.authentication.FSTicketLoginModule): ticket not found!
INFO | jvm 1 | 2014/12/15 16:38:36 | DEBUG 15.12.2014 16:38:36.858 (de.espirit.firstspirit.server.authentication.KerberosLoginModule): initialize...
INFO | jvm 1 | 2014/12/15 16:38:36 | Debug is true storeKey true useTicketCache false useKeyTab true doNotPrompt true ticketCache is null isInitiator false KeyTab is conf/elstar-HTTP.keytab refreshKrb5Config is false principal is HTTP/elstar.e-spirit.de@E-SPIRIT.DE tryFirstPass is false useFirstPass is false storePass is false clearPass is false
INFO | jvm 1 | 2014/12/15 16:38:36 | principal is HTTP/elstar.e-spirit.de@E-SPIRIT.DE
INFO | jvm 1 | 2014/12/15 16:38:36 | Will use keytab
INFO | jvm 1 | 2014/12/15 16:38:36 | Commit Succeeded
INFO | jvm 1 | 2014/12/15 16:38:36 |
INFO | jvm 1 | 2014/12/15 16:38:36 | Found KeyTab conf/elstar-HTTP.keytab for HTTP/elstar.e-spirit.de@E-SPIRIT.DE
INFO | jvm 1 | 2014/12/15 16:38:36 | Found KeyTab conf/elstar-HTTP.keytab for HTTP/elstar.e-spirit.de@E-SPIRIT.DE
INFO | jvm 1 | 2014/12/15 16:38:36 | DEBUG 15.12.2014 16:38:36.860 (de.espirit.firstspirit.server.authentication.KerberosLoginModule): login...
INFO | jvm 1 | 2014/12/15 16:38:36 | DEBUG 15.12.2014 16:38:36.862 (de.espirit.firstspirit.server.authentication.KerberosLoginModule): received SPNEGO Authorization-Header: Negotiate YIIKL...
INFO | jvm 1 | 2014/12/15 16:38:36 | Entered Krb5Context.acceptSecContext with state=STATE_NEW
INFO | jvm 1 | 2014/12/15 16:38:36 | Java config name: null
INFO | jvm 1 | 2014/12/15 16:38:37 | Native config name: /Library/Preferences/edu.mit.Kerberos
INFO | jvm 1 | 2014/12/15 16:38:37 | Loaded from native config
INFO | jvm 1 | 2014/12/15 16:38:37 | >>> KeyTabInputStream, readName(): E-SPIRIT.DE
INFO | jvm 1 | 2014/12/15 16:38:37 | >>> KeyTabInputStream, readName(): HTTP
INFO | jvm 1 | 2014/12/15 16:38:37 | >>> KeyTabInputStream, readName(): elstar.e-spirit.de
INFO | jvm 1 | 2014/12/15 16:38:37 | >>> KeyTab: load() entry length: 62; type: 1
INFO | jvm 1 | 2014/12/15 16:38:37 | >>> KeyTabInputStream, readName(): E-SPIRIT.DE
INFO | jvm 1 | 2014/12/15 16:38:37 | >>> KeyTabInputStream, readName(): HTTP
INFO | jvm 1 | 2014/12/15 16:38:37 | >>> KeyTabInputStream, readName(): elstar.e-spirit.de
INFO | jvm 1 | 2014/12/15 16:38:37 | >>> KeyTab: load() entry length: 62; type: 3
INFO | jvm 1 | 2014/12/15 16:38:37 | >>> KeyTabInputStream, readName(): E-SPIRIT.DE
INFO | jvm 1 | 2014/12/15 16:38:37 | >>> KeyTabInputStream, readName(): HTTP
INFO | jvm 1 | 2014/12/15 16:38:37 | >>> KeyTabInputStream, readName(): elstar.e-spirit.de
INFO | jvm 1 | 2014/12/15 16:38:37 | >>> KeyTab: load() entry length: 70; type: 23
INFO | jvm 1 | 2014/12/15 16:38:37 | >>> KeyTabInputStream, readName(): E-SPIRIT.DE
INFO | jvm 1 | 2014/12/15 16:38:37 | >>> KeyTabInputStream, readName(): HTTP
INFO | jvm 1 | 2014/12/15 16:38:37 | >>> KeyTabInputStream, readName(): elstar.e-spirit.de
INFO | jvm 1 | 2014/12/15 16:38:37 | >>> KeyTab: load() entry length: 86; type: 18
INFO | jvm 1 | 2014/12/15 16:38:37 | >>> KeyTabInputStream, readName(): E-SPIRIT.DE
INFO | jvm 1 | 2014/12/15 16:38:37 | >>> KeyTabInputStream, readName(): HTTP
INFO | jvm 1 | 2014/12/15 16:38:37 | >>> KeyTabInputStream, readName(): elstar.e-spirit.de
INFO | jvm 1 | 2014/12/15 16:38:37 | >>> KeyTab: load() entry length: 70; type: 17
INFO | jvm 1 | 2014/12/15 16:38:37 | Looking for keys for: HTTP/elstar.e-spirit.de@E-SPIRIT.DE
INFO | jvm 1 | 2014/12/15 16:38:37 | Added key: 17version: 3
INFO | jvm 1 | 2014/12/15 16:38:37 | Added key: 18version: 3
INFO | jvm 1 | 2014/12/15 16:38:37 | Added key: 23version: 3
INFO | jvm 1 | 2014/12/15 16:38:37 | Found unsupported keytype (3) for HTTP/elstar.e-spirit.de@E-SPIRIT.DE
INFO | jvm 1 | 2014/12/15 16:38:37 | Found unsupported keytype (1) for HTTP/elstar.e-spirit.de@E-SPIRIT.DE
INFO | jvm 1 | 2014/12/15 16:38:37 | >>> EType: sun.security.krb5.internal.crypto.Aes256CtsHmacSha1EType
INFO | jvm 1 | 2014/12/15 16:38:37 | Using builtin default etypes for permitted_enctypes
INFO | jvm 1 | 2014/12/15 16:38:37 | default etypes for permitted_enctypes: 18 17 16 23.
INFO | jvm 1 | 2014/12/15 16:38:37 | >>> EType: sun.security.krb5.internal.crypto.Aes256CtsHmacSha1EType
INFO | jvm 1 | 2014/12/15 16:38:37 | MemoryCache: add 1418657916/833741/E6F200F634E83162C26058EF73CE9183/isenberg@E-SPIRIT.DE to isenberg@E-SPIRIT.DE|HTTP/elstar.e-spirit.de@E-SPIRIT.DE
INFO | jvm 1 | 2014/12/15 16:38:37 | >>> KrbApReq: authenticate succeed.
INFO | jvm 1 | 2014/12/15 16:38:37 | Krb5Context setting peerSeqNumber to: 277404718
INFO | jvm 1 | 2014/12/15 16:38:37 | Krb5Context setting mySeqNumber to: 277404718
INFO | jvm 1 | 2014/12/15 16:38:37 | >>> Constrained deleg from GSSCaller{UNKNOWN}
INFO | jvm 1 | 2014/12/15 16:38:37 | Debug is true storeKey true useTicketCache false useKeyTab true doNotPrompt true ticketCache is null isInitiator false KeyTab is conf/elstar-HTTP.keytab refreshKrb5Config is false principal is HTTP/elstar.e-spirit.de@E-SPIRIT.DE tryFirstPass is false useFirstPass is false storePass is false clearPass is false
INFO | jvm 1 | 2014/12/15 16:38:37 | principal is HTTP/elstar.e-spirit.de@E-SPIRIT.DE
INFO | jvm 1 | 2014/12/15 16:38:37 | Will use keytab
INFO | jvm 1 | 2014/12/15 16:38:37 | Commit Succeeded
INFO | jvm 1 | 2014/12/15 16:38:37 |
INFO | jvm 1 | 2014/12/15 16:38:37 | DEBUG 15.12.2014 16:38:37.218 (de.espirit.firstspirit.server.authentication.KerberosLoginModule): mechanism: Kerberos 5
INFO | jvm 1 | 2014/12/15 16:38:37 | DEBUG 15.12.2014 16:38:37.218 (de.espirit.firstspirit.server.authentication.KerberosLoginModule): source principal: isenberg@E-SPIRIT.DE
INFO | jvm 1 | 2014/12/15 16:38:37 | DEBUG 15.12.2014 16:38:37.218 (de.espirit.firstspirit.server.authentication.KerberosLoginModule): target principal: HTTP/elstar.e-spirit.de@E-SPIRIT.DE
INFO | jvm 1 | 2014/12/15 16:38:37 | DEBUG 15.12.2014 16:38:37.218 (de.espirit.firstspirit.server.authentication.KerberosLoginModule): Sending SPNEGO Kerberos authentication accept response. WWW-Authenticate: Negotiate oRQwE...
INFO | jvm 1 | 2014/12/15 16:38:37 | DEBUG 15.12.2014 16:38:37.218 (de.espirit.firstspirit.server.authentication.KerberosLoginModule): GSSContext established.
INFO | jvm 1 | 2014/12/15 16:38:37 | DEBUG 15.12.2014 16:38:37.219 (de.espirit.firstspirit.server.authentication.KerberosLoginModule): login successful. principal "isenberg@E-SPIRIT.DE" mapped to FirstSpirit user "isenberg"
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Update for Java 17:
Starting from Java 8 Update 161, the "JCE Unlimited Strength Jurisdiction Policy Files" are included by default in the JDK and JRE. This continues in later versions of Java, including Java 17.
The presented KerberosEncryptionTypes.java file uses dependencies that were not meant for external use and are not exported anymore. Instead, the official exports should be used. I got it working with this code:
import javax.crypto.Cipher;
import javax.crypto.SecretKey;
import javax.crypto.spec.SecretKeySpec;
class KerberosEncryptionTypes {
public static void main(String[] args) throws Exception {
String[] encryptionTypes = {"DES", "DESede", "AES", "ARCFOUR"};
for (String e : encryptionTypes) {
System.out.println("EType: " + e);
try {
SecretKey key = generateKey(e);
System.out.println("Key: " + key.toString());
Cipher cipher = Cipher.getInstance(e);
cipher.init(Cipher.ENCRYPT_MODE, key);
byte[] encrypted = cipher.doFinal("test".getBytes());
System.out.println("Encrypted text: " + new String(encrypted));
} catch (Exception ex) {
System.out.println("Error: " + ex.getMessage());
}
System.out.println();
}
}
private static SecretKey generateKey(String encryptionType) throws Exception {
byte[] keyData = "testtesttesttest".getBytes(); // example key data, adjust length based on algorithm
return new SecretKeySpec(keyData, encryptionType);
}
}| Subject | Latest Article | |
|---|---|---|